How to Get Started
We built the Spectral platform from the ground up to have fantastic developer experience (DX). Spectral Scan is a single self-contained binary, that's easy to get and use.
Your first scan
You can get Spectral in one of the following ways, for your convenience:
Homebrew on mac:
brew tap spectralops/tap && brew install spectralOr, universal installer for mac/Linux:
curl -L https://<YOUR_SPECTRAL_DOMAIN>/latest/x/sh | shreplace <YOUR_SPECTRAL_DOMAIN> with the domain you use to login to SpectralOps (get.spectralops.io, app.spectralops.io etc)
And for Windows PowerShell:
iwr https://<YOUR_SPECTRAL_DOMAIN>/latest/ps1 -useb | iexAll of the above are great. Pick the one you like 🤘
Enterprise customers can use their DSN to get the Spectral enterprise offering, for example:
curl -L https://<YOUR_SPECTRAL_DOMAIN>/latest/sh?dsn=<YOUR_DSN> | sh
Spectral offers several scanning engines. You can read all about it in the Products section.
We'll focus on the Spectral Secret Scanning for this example, so go a head and make your first scan:
$ mkdir spectral-test && cd spectral-test
$ $HOME/.spectral/spectral scan --dsn <YOUR_DSN>
✔ no matches found
scanned 0 bytes and 0 files in 2msAs a security best-practice, you should never run
curl | shblindly. Feel free to inspect our install script (it's a shell script) before running. We also recommend using our very own preflight to verify checksums.
🦸♀️ You're good to go! Looks like everything downloaded right, and things are running!
Your first match
Assuming you're still in spectral-test, let's create a dummy secret:
$ echo AKIAIOSFODNN7EXAMPLX > foo.txt
$ $HOME/.spectral/spectral scan
/Users/superhero/spectral-test/foo.txt
0:20 Error Visible AWS Key CLD001We see our match. We have our file, a location (0:20), severity (Error), description and detector code (CLD001).
Spectral is secure by defaultWe never dump the actual secret or key to the console, or anywhere. If you want to see it, add a
SPECTRAL_SHOW_MATCH=1environment flag before running.
$ $HOME/.spectral/spectral scan
...
[your-project] SVC006 - Exposed PubNub Secret on Client Side App
- res/values/strings.xmlKicking the tires 💥
To get an idea of the amount of stacks Spectral can analyze, you can use our codesec-goat repo.
What's a "goat" project?A common saying is that if your fence won't hold water, it won't hold a goat. Animals are very creative, and will find a way around your barriers. In the same funny analogy, a goat repo demonstrates creativity and deliberate security issues that you might not expect.
Assuming you unzipped codesec-goat somewhere, let's run Spectral scan:
$ cd codesec-goat
$ $HOME/.spectral/spectral scan➜ spectral-goat git:(master) spectral scan
__ .__
___________ _____ ______/ |_____________ | |
/ ___\____ \/ _ / ___\ __.| __/\__ \ | |
\___ \| |_> \ ___\ \___| | | | / __ \| |_
/______| __/ \_____\_____|__| |__| /______|___/ops.io
|__|
Spectral: 1.9.131 (1602)
OS: macos (x86_64)
is_audit: No
DSN: Yes (from param/env)
mode: interactive
is_public: n/a
repo: https://github.com/spectral-corp/spectral-goat
branch: master
remote_cfg: Yes
High: Visible Google API Key [CLD004]
╭─[src/infra/google-api.json:24:27]
│
24 │ "current_key": "AIzaSyAM*******************************"
· ───────────────────┬───────────────────
· ╰───────────────────── Visible Google API Key
────╯
Medium: Visible Google cloud host [CLD030]
╭─[src/infra/google-api.json:18:25]
│
18 │ "client_id": "344570128040-0a*********************************************************",
· ────────────────────────────────────┬───────────────────────────────────
· ╰───────────────────────────────────── Visible Google cloud host
────╯
Medium: Visible Google cloud host [CLD030]
╭─[src/infra/google-api.json:31:29]
│
31 │ "client_id": "344570128040-0a*********************************************************",
· ────────────────────────────────────┬───────────────────────────────────
· ╰───────────────────────────────────── Visible Google cloud host
────╯
High: Google Client ID URL [GOOG001]
╭─[src/infra/google-api.json:18:25]
│
18 │ "client_id": "344570128040-0a*********************************************************",
· ────────────────────────────────────┬───────────────────────────────────
· ╰───────────────────────────────────── Google Client ID URL
────╯
High: Google Client ID URL [GOOG001]
╭─[src/infra/google-api.json:31:29]
│
31 │ "client_id": "344570128040-0a*********************************************************",
· ────────────────────────────────────┬───────────────────────────────────
· ╰───────────────────────────────────── Google Client ID URL
────╯
High: Visible Private Key [KEYS002]
╭─[src/infra/rsa.key:1:1]
│
1 │ ╭─▶ -----BEGIN RSA PRIVATE KEY-----
⋮ ⋮
27 │ ├─▶ *****************************
· │
· ╰─────────────────────────────────── Visible Private Key
────╯
High: Visible Private Key [KEYS002]
╭─[src/infra/id_rsa:1:1]
│
1 │ ╭─▶ -----BEGIN OPENSSH PRIVATE KEY-----
⋮ ⋮
38 │ ├─▶ *********************************
· │
· ╰─────────────────────────────────────── Visible Private Key
────╯
High: MemCached configured to run as root [MEMC002]
╭─[src/infra/memcache/memcached.conf:30:1]
│
30 │ *******
· ───┬───
· ╰───── MemCached configured to run as root
────╯
Medium: MySQL config file contains a visible report password [MYSQL003]
╭─[src/infra/mysql/mysqld.cnf:24:21]
│
24 │ report-password = **** # bad password
· ──┬─
· ╰─── MySQL config file contains a visible report password
────╯
Medium: Redis configuration include one or more users with a visible password [REDIS001]
╭─[src/infra/redis/redis.conf:16:31]
│
16 │ user shai on +@all -DEBUG ~* >************ -@all
· ──────┬─────
· ╰─────── Redis configuration include one or more users with a visible password
────╯
Medium: Redis configured to worldwide listening [REDIS003]
╭─[src/infra/redis/redis.conf:8:1]
│
8 │ bind *****************
· ───────────┬───────────
· ╰───────────── Redis configured to worldwide listening
───╯
Informational: Potential cryptographic key bundle file [SENF006]
╭─[/Users/jenia/dev/spectral-goat/src/notebook/docs/source/ipython_security.asc]
│
────╯
Medium: Google Services JSON File [SENF086]
╭─[/Users/jenia/dev/spectral-goat/src/infra/google-api.json]
│
────╯
Medium: Found a SQLite database file [SENF106]
╭─[/Users/jenia/dev/spectral-goat/src/notebook/notebook/tests/test_hist.sqlite]
│
────╯
Informational: Exposed Sentry DSN [SVC016]
╭─[src/frontend/sentry.js:9:9]
│
9 │ dsn: 'https://3427253**********************************************************',
· ────────────────────────────────────┬────────────────────────────────────
· ╰────────────────────────────────────── Exposed Sentry DSN
───╯
High: Visible Terraform Azure Database password [TF010]
╭─[src/multicloud/terraform/azure/main.tf:12:35]
│
12 │ administrator_login_password = "4-v3r*****************"
· ───────────┬──────────
· ╰──────────── Visible Terraform Azure Database password
────╯
Medium: Visible Terraform Azure Database username [TF011]
╭─[src/multicloud/terraform/azure/main.tf:11:35]
│
11 │ administrator_login = "*************"
· ──────┬──────
· ╰──────── Visible Terraform Azure Database username
────╯
✖ found 17 matches
scanned 10515636 bytes and 557 files in 507msYou'll see a wealth of findings ranging around the following topics:
- Sensitive data
- Credentials and access controls
- Misconfiguration
- Tech stack bad practices
🦸♀️ Human error is, well, complicated. You may detect SQL injection, update libraries every day, still -- takes one innocent mistake to expose your team to unneeded risk.
Our idea is: we build an understanding of everything that can lead to security minded human errors, and poses a high risk. Then we look for it, detect it, and help you block and mitigate it.
Make it stick
Now that you've seen what Spectral can do, you can plug it into your development processes so that you're safe all the time. Like any new process for a dev team, we need to make the process stick.
One of the most recommended places to integrate Spectral to is your CI.
Never hold up a buildWe build Spectral for performance. Every day. That's actually a business KPI of ours. Spectral scans an average sized repo in a second. Thanks to Rust and our low-level engineers, we're very happy.
Let's see how Spectral works in CircleCI (we support every popular CI there is today):
Before
version: 2
jobs:
build:
docker:
- image: circleci/node:latest
steps:
- checkout
- run: yarn testNow you need to add your TEAM_KEY and your SPECTRAL_DSN to CircleCI (look here for how to do that). And use this configuration:
version: 2
jobs:
build:
docker:
- image: circleci/node:latest
steps:
- checkout
- curl -L 'https://get.spectralops.io/latest/sh?key=${TEAM_KEY}' | sh
- $HOME/.spectral/spectral run
- run: yarn testAs a security best-practice, you should never run
curl | shblindly. Feel free to inspect our install script (it's a shell script) before running or store it in your repo for safekeeping. We also recommend using our very own preflight to verify checksums.
Data privacy: never see, never store policySpectral never sees your code or data, it never leaves your data center, and we never store any of your private code or data. We do this by packing all of our technology inside Spectral scan, so we don't need a backend.
Our scanner sends back only metadata (file names, match location, primarily) so that we can show you where your problems are in our SaaS.
Now, you should both have nice reporting in your CI and in your Spectral account:
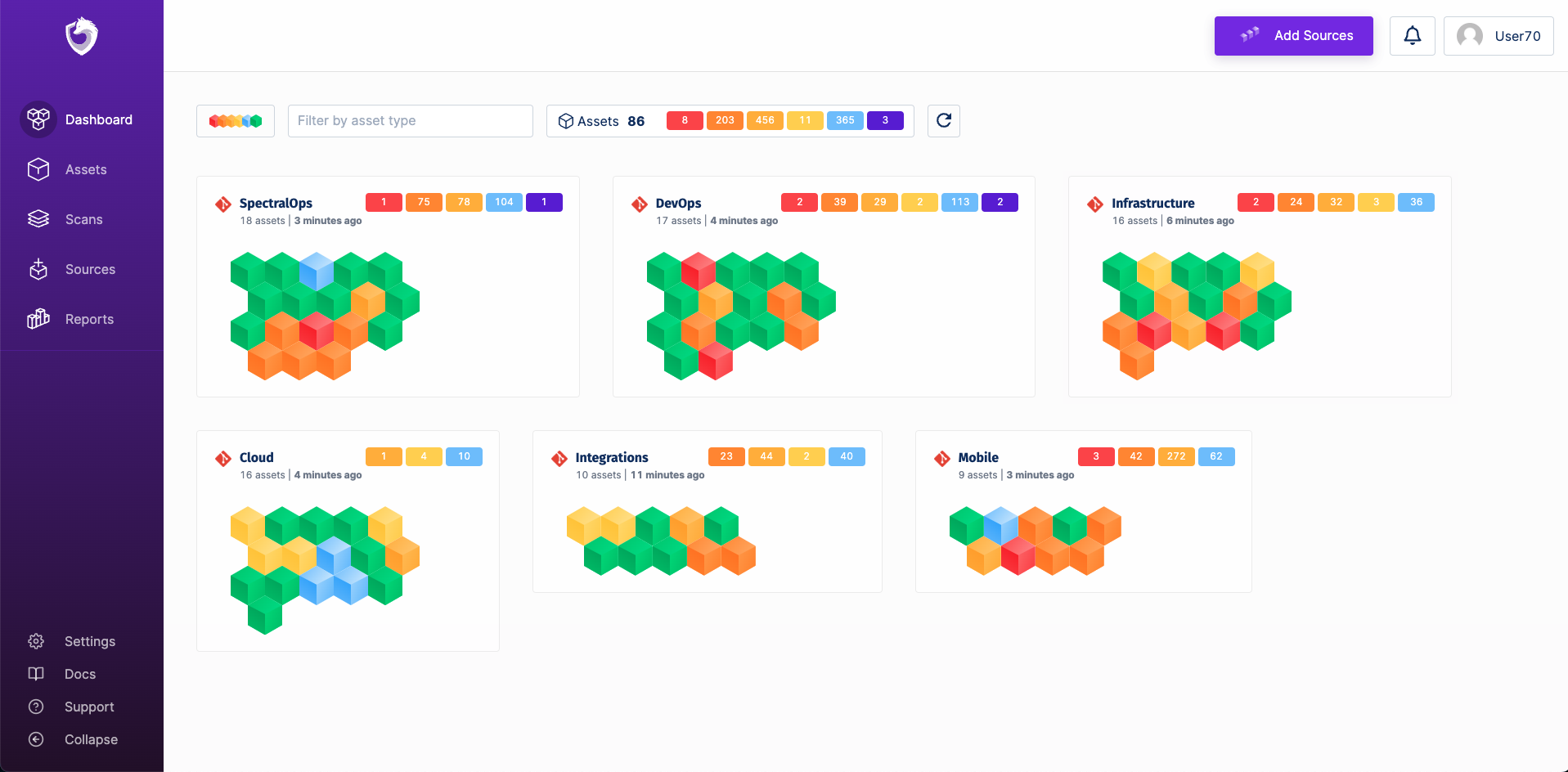
🦸♀️ Auto discovery in action! Your organization, teams, assets are auto-discovered and configured in your dashboard. We use the metadata your scanner is sending. No setup needed!
Updated 6 months ago